| New Threat Detection Added | 2 (PlugX RAT and Carbon Paper Malware) |
| New Threat Protections | 105 |
Weekly Detected Threats
The following threats were added to Crystal Eye XDR this week:
Threat name: | PlugX RAT | |||||||||||||||||||||
RATs aim to remotely control devices with various functions. PlugX, for instance, utilises DLL sideloading to infiltrate devices, hiding malicious payloads within benign executables. Recently, a variant emerged, spreading across multiple countries, monitoring USB devices for further infection. It hides files on the Windows OS, visible only on Unix-like systems. This variant also creates a concealed directory, possibly for stolen data. Since December 2022, PlugX has used HTML smuggling to deliver malware, bypassing traditional security measures. Darktrace observed PlugX activity, detecting C2 communications within customer networks, enabling swift response to mitigate threats. Suspicious connections to rare endpoints on ports like 110, 443, 5938, and 80 were noted. | ||||||||||||||||||||||
Threat Protected: | 05 | |||||||||||||||||||||
Rule Set Type: |
| |||||||||||||||||||||
Class Type: | Trojan-activity | |||||||||||||||||||||
Kill Chain: |
| |||||||||||||||||||||
Threat name: | Carbon Paper Malware | ||||||||||||||||||
The Turla espionage group has long targeted various institutions. Recently, we discovered new versions of Carbon, a backdoor in their arsenal. Swiss GovCERT.ch analysed this component last year after an attack on RUAG, a Swiss government-owned defence firm. Our blog post highlights technical innovations in the latest Carbon versions. The group continuously develops Carbon, as evidenced by the internal version changes. They alter tools once exposed. Carbon is deployed after reconnaissance, often initiated through spearphishing or watering hole attacks. It's a sophisticated backdoor aimed at stealing sensitive data. Sharing similarities with "Uroburos," Carbon serves as a communication channel between malware components, offering fewer features than its predecessor. It's deployed after a reconnaissance tool confirms the target's significance. | |||||||||||||||||||
Threat Protected: | 02 | ||||||||||||||||||
Rule Set Type: |
| ||||||||||||||||||
Class Type: | Trojan-activity | ||||||||||||||||||
Kill Chain: |
| ||||||||||||||||||
Known exploited vulnerabilities (Week 4 - April 2024)
Threat | CVSS | Description | |
CVE-2022-38028 | 7.8 (High) | Microsoft Windows Print Spooler Privilege Escalation Vulnerability | |
CVE-2024-4040 | 10.0 (Critical) | CrushFTP VFS Sandbox Escape Vulnerability | |
CVE-2024-20359 | 6.0 (Medium) | Cisco ASA and FTD Privilege Escalation Vulnerability | |
CVE-2024-20353 | 8.6 (High) | Cisco ASA and FTD Denial of Service Vulnerability |
Updated Malware Signatures (Week 4 - April 2024)
Threat | Description | |
Upatre | Upatre is also a malware dropper that downloads additional malware on an infected machine. It is usually observed to drop banking trojan after the initial infection. | |
Remcos | Remcos functions as a remote access trojan (RAT), granting unauthorised individuals the ability to issue commands on the compromised host, record keystrokes, engage with the host's webcam, and take snapshots. Typically, this malicious software is distributed through Microsoft Office documents containing macros, which are often attached to malicious emails. | |
QuasarRat | A remote access trojan that was made available to the public as an open-source project. Once installed on a victim’s machine, it is capable of keylogging, data and screen capturing among other things. It is also known to be highly customisable depending on the threat actor’s intended need. | |
Bifrost | A remote access trojan that enables its operator to take control of a victim machine and steal data. It is usually distributed through spam and phishing emails. |
| Ransomware Report | |
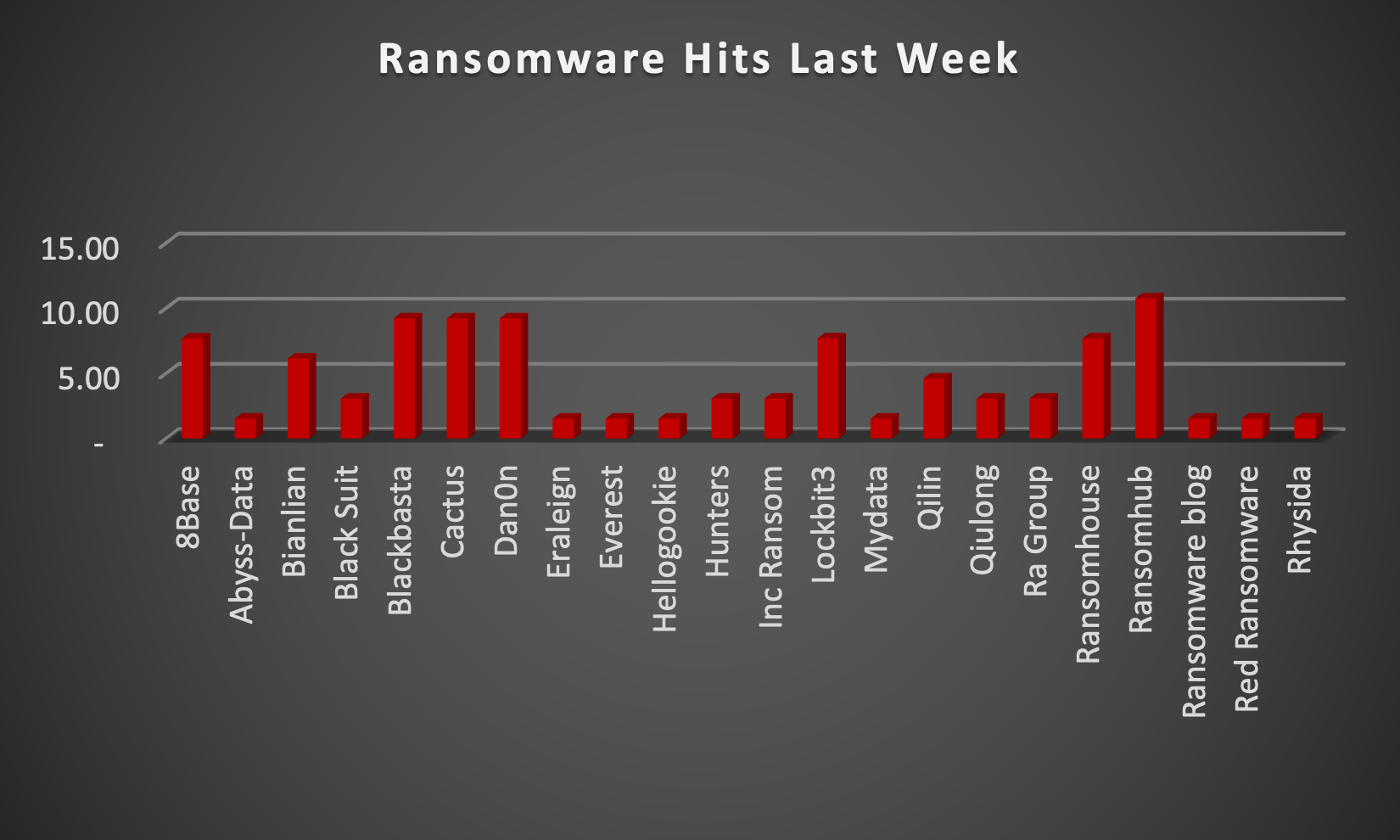
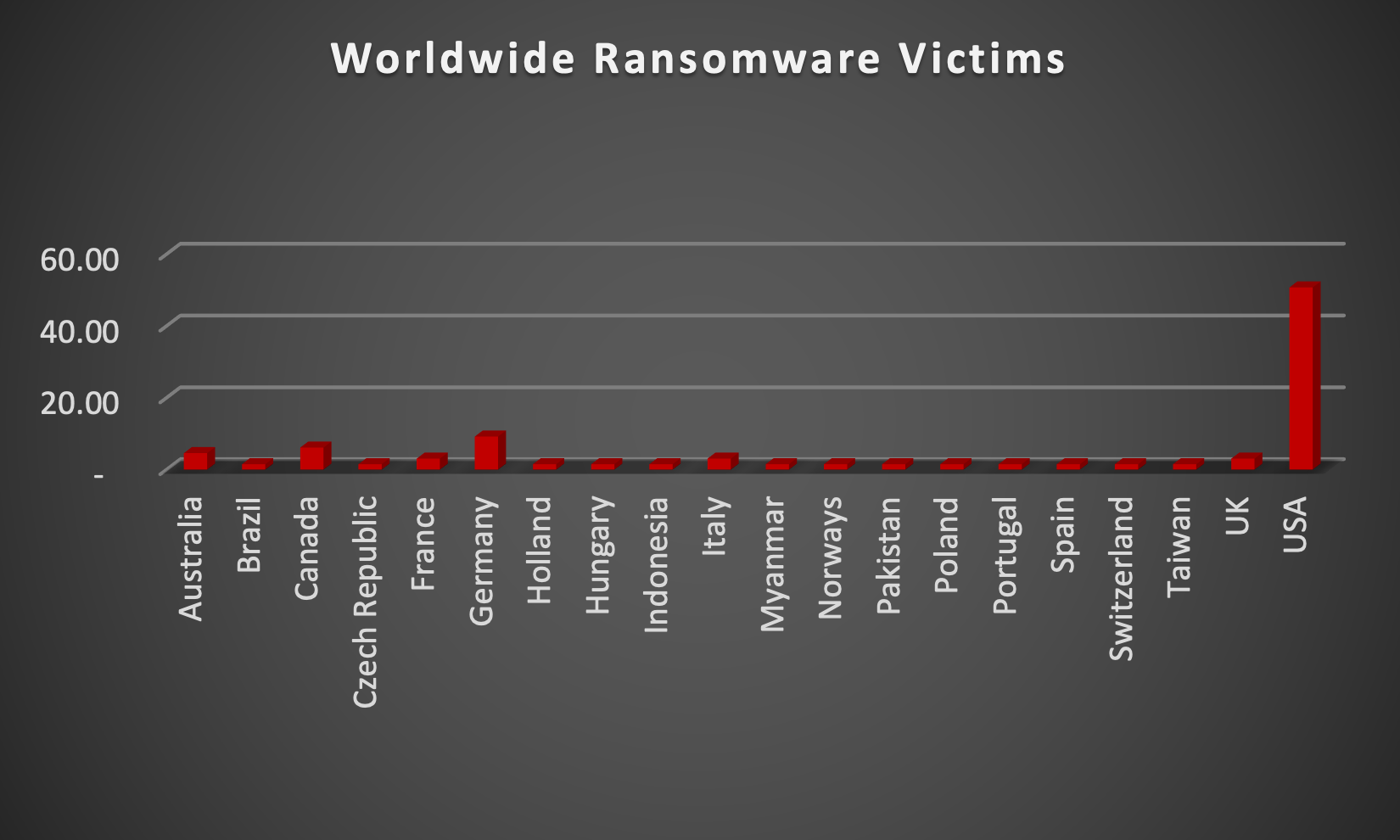
The Red Piranha Team actively collects information on organisations globally affected by ransomware attacks from various sources, including the Dark Web. In the past week alone, our team uncovered new ransomware victims and updates on previous victims across 16 different industries spanning 20 countries. This underscores the widespread and indiscriminate impact of ransomware attacks, emphasising their potential to affect organisations of varying sizes and sectors worldwide. RansomHub ransomware stands out as the most prolific, having updated a significant number of victims (10%) distributed across multiple countries. In comparison, Blackbasta, Cactus and Dan0n ransomware updated 9% victims each, in the past week. The following list provides the victim counts in percentages for these ransomware groups and a selection of others. | |
| Name of Ransomware Group | Percentage of new Victims last week |
Abyss-Data | 1.54% |
Bianlian | 6.15% |
Black Suit | 3.08% |
Blackbasta | 9.23% |
Cactus | 9.23% |
Dan0n | 9.23% |
Eraleign | 1.54% |
Everest | 1.54% |
Hellogookie | 1.54% |
Hunters | 3.08% |
Inc Ransom | 3.08% |
Lockbit3 | 7.69% |
Mydata | 1.54% |
Qilin | 4.62% |
Qiulong | 3.08% |
Ra Group | 3.08% |
Ransomhouse | 7.69% |
RansomHub | 10.77% |
Ransomware blog | 1.54% |
Red Ransomware | 1.54% |
Rhysida | 1.54% |
RansomHub Ransomware Group RansomHub is a relatively new ransomware group that emerged in late 2020. They distinguish themselves from other ransomware groups by offering a supposedly better deal to affiliates and having stricter controls in place. Notably, they also claim to avoid targeting non-profit organisations. However, there's some evidence suggesting a potential link between RansomHub and ALPHV, a previous ransomware group. Given RansomHub's recent emergence, its future operations and attack patterns remain unclear. Here's a comprehensive overview of RansomHub ransomware: Tactics, Techniques, and Procedures (TTPs) Initial Access Vectors: RansomHub employs various methods to gain initial access into a victim's network, including:
Data Exfiltration: RansomHub exfiltrates sensitive data from compromised systems, potentially including financial records, personal information, and intellectual property. Encryption: RansomHub encrypts files on infected devices, rendering them inaccessible and demanding a ransom payment for decryption. Leak Threats: RansomHub maintains a leak site on the dark web where they threaten to publish stolen data if the ransom is not paid. Ransom Note: Kill Chain:
Indicators of Compromise (IOCs)
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
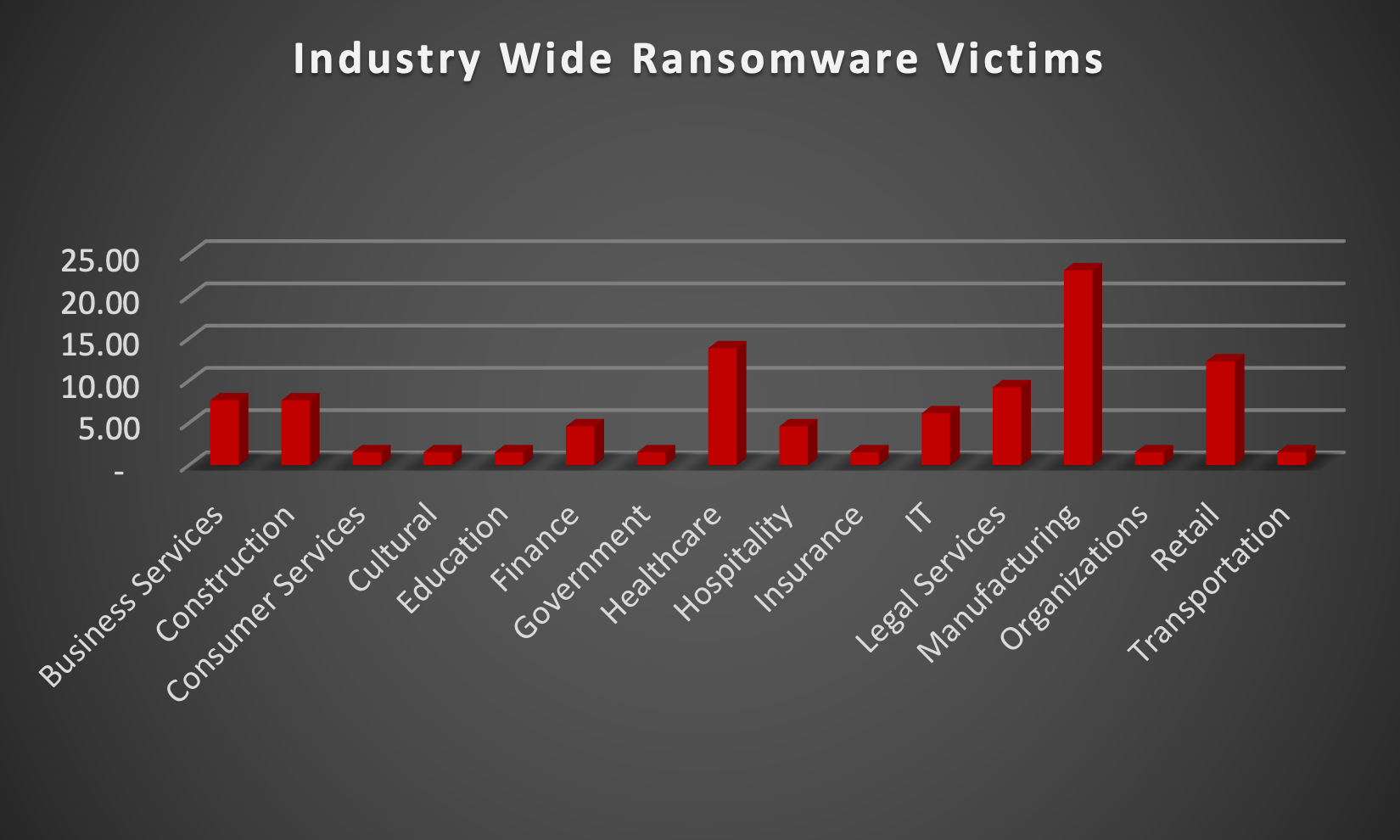
Upon further investigation, it has been identified that ransomware has left its mark on 16 different industries worldwide. Notably, the Manufacturing industry bore the brunt of the attacks in the past week, accounting for 23% of victims. There are a few key reasons why the manufacturing sector is a prime target for ransomware groups:
- High Disruption Potential: Manufacturing relies heavily on interconnected systems and just-in-time production. A ransomware attack can grind operations to a halt, causing significant financial losses due to production delays and lost revenue. This pressure to get back online quickly can make manufacturers more willing to pay the ransom.
- Vulnerable Legacy Systems: Many manufacturers use legacy control systems (OT) that haven't been updated for security. These older systems often lack robust security features, making them easier targets for attackers to exploit.
- Limited Cybersecurity Investment: Traditionally, cybersecurity might not have been a top priority for some manufacturers compared to production efficiency. This lack of investment in security awareness training and robust security protocols leaves them exposed.
- Valuable Data: Manufacturing facilities often hold valuable intellectual property (IP) and trade secrets. Ransomware groups may not only disrupt operations but also threaten to leak this sensitive data if the ransom isn't paid.
- Success Breeds Success: The high payout potential from past attacks on manufacturers incentivises ransomware groups to continue targeting them.
The table below delineates the most recent ransomware victims, organised by industry, shedding light on the sectors grappling with the significant impact of these cyber threats.
Name of the affected Industry | Victims Count (%) |
Business Services | 7.69% |
Construction | 7.69% |
Consumer Services | 1.54% |
Cultural | 1.54% |
Education | 1.54% |
Finance | 4.62% |
Government | 1.54% |
Healthcare | 13.85% |
Hospitality | 4.62% |
Insurance | 1.54% |
IT | 6.15% |
Legal Services | 9.23% |
Manufacturing | 23.08% |
Organisations | 1.54% |
Retail | 12.31% |
Transportation | 1.54% |